第 7 课 补充讲义
算术化是将计算编码为代数约束满足问题的过程。这将检验其正确性的复杂性降低到少量概率代数检查。在证明系统中,算术化的选择会影响IOP的选择范围(见图1)。
图1:证明系统的组成部分。请回顾第5讲(承诺方案)中,承诺方案可用于将交互式预言机证明(IOP)编译成证明系统。
英文原文
Arithmetisation is the encoding of a computation as an algebraic constraint satisfaction problem. This reduces the complexity of verifying its correctness to a few probabilistic algebraic checks. In a proof system, the choice of arithmetisation limits the corresponding range of IOPs that can be used to check it (see Figure 1).
Figure 1: The components of a proof system. Recall from Lecture 3 (Commitment Schemes) that a commitment scheme can be used to compile an interactive oracle proof (IOP) into a proof system.
二次算术程序 (QAPs)
二次算术程序(Quadratic Arithmetic Program,QAP) [9] 是一种将语句转换为多项式上二次方程组的方式。它们可以通过线性交互式证明(LIPs)[10],代数IOPs [6],多线性IOPs ([14],[15]) 进行检验。任何具有乘性复杂度
定义1.1. 二次算术程序(QAP)
一个度数为
其中
英文原文
The Quadratic Arithmetic Program (QAP) [9] is a way to translate statements into a system of quadratic equations over polynomials. They can be checked by linear interactive proofs (LIPs) [10], algebraic IOPs [6], multilinear IOPs ([14], [15]). Any circuit with multiplicative complexity
Definition 1.1. [Quadratic Arithmetic Program (QAP)]
A Quadratic Arithmetic Program Q of degree
where
一阶约束系统 (R1CS)
算术电路可以用简化形式的一阶约束系统(R1CS)表示,而R1CS则可以转换为QAP。
| 参数系统 | 算术化 | 信息理论协议 | 密码编译器 |
|---|---|---|---|
| Groth16 [10] | R1CS | 线性交互证明 (LIP) | 双线性配对 |
| Marlin [6] | R1CS | 代数全息证明 (AHP) | 改进的KZG承诺 |
| Spartan [15] | R1CS | 变体的sumcheck协议 | SPARK |
| Dory [14] | R1CS | 多线性IOP | 双线性配对 |
| Nova [13] | 放宽的R1CS | 多线性IOP | 多线性PCS |
表1:使用R1CS算术化的证明系统的示例。
在第二讲(Circom 1)中,我们看到了IsZero电路,它检查给定值是否为零的声明。让我们将IsZero转换为一个R1CS电路,然后将其转换为QAP。
template IsZero(){
signal input in;
signal output out;
signal inv;
inv <−− in != 0 ? 1 / in : 0;
out <== −in * inv + 1;
in * out === 0;
}template IsZero(){
signal input in;
signal output out;
signal inv;
inv <−− in != 0 ? 1 / in : 0;
out <== −in * inv + 1;
in * out === 0;
}代码1:从comparators.circom中获取的IsZero电路。
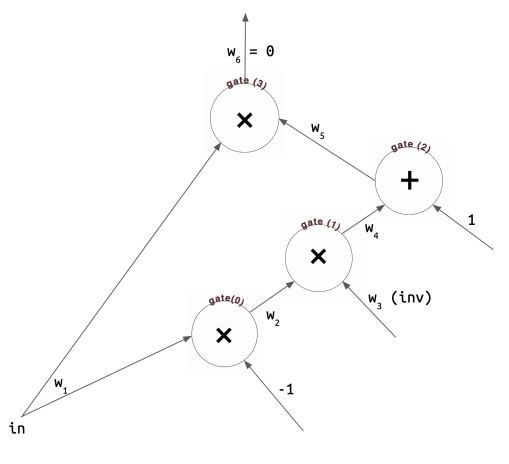
circom的IsZero程序可以“展平”为四个约束条件,每个都采用 左侧 o 右侧 = output 的形式:
在算术电路表示中(左图),每个约束条件对应于一个加法或乘法门。
证明人声称知道一些合法的赋值
现在,我们将每个左边的
矩阵
英文原文
Arithmetic circuits can be expressed a simplified form known as Rank-1 Constraint System (R1CS), which can in turn be transformed into a QAP.
| Argument system | Arithmetization | Information-theoretic protocol | Cryptographic compiler |
|---|---|---|---|
| Groth16 [10] | R1CS | linear interactive proof (LIP) | bilinear pairings |
| Marlin [6] | R1CS | algebraic holographic proof (AHP) | adapted KZG commitment |
| Spartan [15] | R1CS | variant of sumcheck protocol | SPARK |
| Dory [14] | R1CS | multilinear IOP | bilinear pairings |
| Nova [13] | Relaxed R1CS | multilinear IOP | multilinear PCS |
Table 1: Examples of proof systems which make use of R1CS arithmetisation.
In Lecture 2 (Circom 1), we saw the Is Zero circuit, which checks a claim about whether a given value is zero. Let's convert Is eero into an R1CS circuit, and then transform it into a QAP.
template IsZero(){
signal input in;
signal output out;
signal inv;
inv <−− in != 0 ? 1 / in : 0;
out <== −in * inv + 1;
in * out === 0;
}template IsZero(){
signal input in;
signal output out;
signal inv;
inv <−− in != 0 ? 1 / in : 0;
out <== −in * inv + 1;
in * out === 0;
}Listing 1: The Iszero circuit, taken from comparators. circom in circomlib.

The circom Iszero program can be "flattened" into four constraints, each of the form left o right = output:
In the arithmetic circuit representation (left), each of these constraints corresponds to an addition or multiplication gate.
The prover is claiming to know some legal assignment
Now, we collect each of the left
The
R1CS 至 QAP
回顾一下对于度数为
为了将我们的
让我们看一下
因此,
(注意:构造
数学基础知识:拉格朗日插值
给定点和评估
其中,
当评估域为
当评估域为
QAP算术化引出了验证指数中的等式的协议。由于我们目前只有
| 参数系统 | 算术化 | 信息论协议 | 密码编译器 |
|---|---|---|---|
| STARK [2] | AIR | 代数链接IOP (使用FRI作为RS-IOPP) | Merkle树 |
| PlonK [8] | RAP | 多项式IOP | KZG承诺 |
| Halo 2 ([3],[4]) | RAP | 多项式IOP | 内积证明 |
表2: 例子证明系统使用AIR、PAIR和RAP算术化。
英文原文
Recall the definition 1.1 of a QAP of degree
To convert our
Let's take a look at gate
So
(NB: To construct the
Math building block: Lagrange interpolation
Given points and evaluations
where
When the evaluation domain is
When the evaluation domain is
The QAP arithmetisation induces protocols that verify equations on a secret element in the exponent. Since we currently only have cryptographic
| Argument system | Arithmetization | Information-theoretic protocol | Cryptographic compiler |
|---|---|---|---|
| STARK [2] | AIR | algebraic linking IOP (uses FRI as RS-IOPP) | Merkle trees |
| PlonK [8] | RAP | polynomial IOP | KZG commitment |
| Halo 2 ([3],[4]) | RAP | polynomial IOP | inner product argument |
Table 2: Examples of proof systems which make use of AIR, PAIR, and RAP arithmetisations.
代数中间表示 (AIR)
代数中间表示(Algebraic Intermediate Representation,AIR)是由一组均匀计算(uniform computations)组成的程序表示。一个在域
Fibonacci 数列的 AIR
我们可以使用两个状态转换多项式来指定 Fibonacci 数列的 AIR 程序:
例如,我们可以检查在第
| 1 | 1 | |
| 2 | 3 | |
| 5 | 8 | |
| 13 | 21 |
练习:你能修改这个程序,使其成为宽度为 3 的 AIR 吗?
数学基础
单位根。AIR 将值列
这让我们通过乘以
英文原文
An Algebraic Intermediate Representation (AIR) [16] is a representation of a program consisting of uniform computations. An AIR
AIR for Fibonacci sequence
We can specify an AIR program for the Fibonacci sequence using two state transition polynomials:
As an example, let's check that the state transition holds on row
| 1 | 1 | |
| 2 | 3 | |
| 5 | 8 | |
| 13 | 21 |
Exercise: can you modify this program to make an AIR of width 3?
Math building block
Roots of unity. AIR encodes a column of values
This lets us "shift" up and down rows by multiplying by a factor of
预处理的 AIR (PAIR)
在预处理的AIR(PAIR)中,我们引入了
PAIR加法和乘法
让我们构建一个PAIR,在其中对某些行执行加法,对其他行执行乘法。为此,我们定义“加法选择器”
让我们在
以及在
| 1 | 0 | 0 | 1 | |
| 0 | 1 | 1 | 2 | |
| 1 | 1 | 2 | 2 | |
| 0 | 1 | 4 | 0 |
英文原文
In a Preprocessed AIR, or PAIR, we introduce
PAIR for addition and multiplication
Let's construct a PAIR where we perform an addition on some rows, and a multiplication on other rows. For this purpose, we define the "addition selector"
Let's check the constraint on row
and row
| 1 | 0 | 0 | 1 | |
| 0 | 1 | 1 | 2 | |
| 1 | 1 | 2 | 2 | |
| 0 | 1 | 4 | 0 |
带预处理的随机化 AIR (RAP)
具有预处理的随机AIR(RAP)允许交互轮次引入验证器随机性。在稍后的轮次中,可以将较早轮次的随机性用作约束中的变量。这使得本地约束(相邻行之间)可以检查全局属性。
RAP用于多重集合相等性
假设我们有一个宽度为2的AIR,并且想要检查一列中的值
为了在两列所有行上检查这个“大乘积”,证明者使用验证器挑战
在最后一行
练习题:你能写一个仅在行
为了说明多重集合相等性检查,让我们考虑一个
| 1 | |||
| 0 | 0 |
在每个步骤中,我们检查约束
例如,将其应用于第
这个检查归纳地检查了
英文原文
A Randomised AIR with Preprocessing (RAP) allows for rounds of interaction to introduce verifier randomness. In a later round, randomness from the earlier rounds can be used as variables in constraints. This enables local constraints (between adjacent rows) to check global properties.
RAP for multiset equality
Suppose that we had a width-2 AIR and wanted to check that the values in one column
To check this "grand product" over all rows of both columns, the prover uses the verifier challenge
At the final row
Exercise: can you write a constraint that applies only on the row
To illustrate the multiset equality check, let us consider an example where
| 1 | |||
| 0 | 0 |
At each step, we check the constraint
As an example, applying this on the row
This inductively checks that
其他算术化技术
这里未涵盖的一些算术化方法包括:分层算术电路、布尔电路和布尔超立方体。这些方法有时会超出IOP等的信息理论模型,例如“头脑中的多方计算”[12]。在第9讲中,我们将分析选择适当的算术化方法的一些因素。
| 参数系统 | 算术化 | 信息理论协议 | 密码编译器 |
|---|---|---|---|
| Virgo [17] | 分层算术电路 | GKR协议IOP | Merkle树 |
| Ligero [1] | 算术电路 | 头脑中MPC,ZKIPCP | Merkle树 |
| BooLigero [11] | 布尔电路 | 头脑中MPC,IOP | Ligero |
| HyperPlonK [5] | 布尔超立方体 | sumcheck协议 (多线性IOP) | 多线性PCS |
表3:其他算术化方法的一些示例。
英文原文
Some arithmetisations not covered here include: layered arithmetic circuits, Boolean circuits, and the Boolean hypercube. These sometimes lend themselves to information-theoretic models beyond the IOP, such as MPC-in-the-head [12]. In Lecture 9 (Proving Systems Stack; Recursion and Proof Composition), we will analyse some of the factors that go into picking a suitable arithmetisation.
| Argument system | Arithmetization | Information-theoretic protocol | Cryptographic compiler |
|---|---|---|---|
| Virgo [17] | layered arithmetic circuits | GKR protocol IOP | Merkle tree |
| Ligero [1] | arithmetic circuits | MPC-in-the-head, ZKIPCP | Merkle tree |
| BooLigero [11] | Boolean circuits | MPC-in-the-head, IOP | Ligero |
| HyperPlonK [5] | Boolean hypercube | sumcheck protocol (multilinear IOP) | multilinear PCS |
Table 3: Some examples of other arithmetisations.
参考文献
[1] S. Ames, C. Hazay, Y. Ishai, and M. Venkitasubramaniam. Ligero: Lightweight sublinear arguments without a trusted setup. In Proceedings of the 2017 acm sigsac conference on computer and communications security, pages 2087–2104, 2017.
[2] E. Ben-Sasson, I. Bentov, Y. Horesh, and M. Riabzev. Scalable, transparent, and postquantum secure computational integrity. Cryptology ePrint Archive, 2018. [3] S. Bowe, J. Grigg, and D. Hopwood. Recursive proof composition without a trusted setup. Cryptology ePrint Archive, 2019.
[4] S. Bowe, D. Hopwood, and J. Grigg. The halo2 Book: Protocol Description. https://zcash.github.io/halo2/design/protocol.html, 2020.
[5] B. Chen, B. Bünz, D. Boneh, and Z. Zhang. Hyperplonk: Plonk with linear-time prover and high-degree custom gates. Cryptology ePrint Archive, 2022.
[6] A. Chiesa, Y. Hu, M. Maller, P. Mishra, N. Vesely, and N. Ward. Marlin: preprocessing zkSNARKs with universal and updatable SRS. In Annual International Conference on the Theory and Applications of Cryptographic Techniques, pages 738–768. Springer, 2020.
[7] A. Gabizon. From AIRs to RAPs - how PLONK-style arithmetization works. https://hackmd.io/@aztec-network/plonk-arithmetiization-air, 2020.
[8] A. Gabizon, Z. J. Williamson, and O. Ciobotaru. Plonk: Permutations over lagrange-bases for oecumenical noninteractive arguments of knowledge. Cryptology ePrint Archive, 2019.
[9] R. Gennaro, C. Gentry, B. Parno, and M. Raykova. Quadratic span programs and succinct NIZKs without PCPs. In Annual International Conference on the Theory and Applications of Cryptographic Techniques, pages 626–645. Springer, 2013.
[10] J. Groth. On the size of pairing-based non-interactive arguments. In Annual international conference on the theory and applications of cryptographic techniques, pages 305–326. Springer, 2016.
[11] Y. Gvili, S. Scheffler, and M. Varia. Booligero: improved sublinear zero knowledge proofs for boolean circuits. In International Conference on Financial Cryptography and Data Security, pages 476–496. Springer, 2021.
[12] Y. Ishai, E. Kushilevitz, R. Ostrovsky, and A. Sahai. Zero-knowledge from secure multiparty computation. In Proceedings of the thirty-ninth annual ACM symposium on Theory of computing, pages 21–30, 2007.
[13] A. Kothapalli, S. Setty, and I. Tzialla. Nova: Recursive zero-knowledge arguments from folding schemes. In Advances in Cryptology–CRYPTO 2022: 42nd Annual International Cryptology Conference, CRYPTO 2022, Santa Barbara, CA, USA, August 15–18, 2022, Proceedings, Part IV, pages 359–388. Springer, 2022.
[14] J. Lee. Dory: Efficient, transparent arguments for generalised inner products and polynomial commitments. In Theory of Cryptography Conference, pages 1–34. Springer, 2021.
[15] S. Setty. Spartan: Efficient and general-purpose zkSNARKs without trusted setup. In Annual International Cryptology Conference, pages 704–737. Springer, 2020.
[16] StarkWare. ethSTARK Documentation. Cryptology ePrint Archive, Paper 2021/582, 2021. https://eprint.iacr.org/2021/582.
[17] J. Zhang, T. Xie, Y. Zhang, and D. Song. Transparent polynomial delegation and its applications to zero knowledge proof. In 2020 IEEE Symposium on Security and Privacy (SP), pages 859–876. IEEE, 2020.