第 5 课 补充讲义
现代 SNARK 由两个部分组成:信息论交互式预言机证明 (IOP) [1]; 和一个兼容的密码承诺方案,它将 IOP“编译”成一个论证系统 [5]。 本讲义介绍几种常用的承诺方案。
IOP 是“信息论的”,因为即使针对 计算无界 的证明者和验证者,它也能提供可靠性和零知识保证。 为了使这成为可能,证明系统做出了“预言机访问”的理想化假设:换句话说,验证者只能通过随机查询访问证明者的消息。
承诺方案使用密码原语(例如单向函数)实例化此预言机访问:因此,由此产生的论证系统仅对于 计算有界 的证明者和验证者而言是安全的。 为了实现 简洁 的论证系统,所选择的承诺方案必须提供相对于被证明的计算而言较低的通信复杂性。
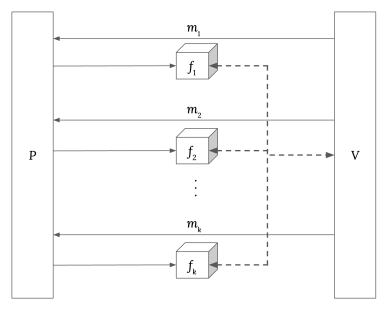
图 1:
英文原文
Modern SNARKs consist of two components: an information-theoretic interactive oracle proof (IOP) [1]; and a compatible cryptographic commitment scheme, which "compiles" the IOP into an argument system [5]. This note introduces several commonly used commitment schemes.
An IOP is "information-theoretic" in that it provides soundness and zero-knowledge guarantees even when the prover and verifier are computationally unbounded. To make this possible, the proof system makes the idealised assumption of "oracle access": in other words, the verifier can only access the prover's messages through random queries.
The commitment scheme instantiates this oracle access using cryptographic primitives (e.g. a one-way function): as a consequence, the resulting argument system is only secure with respect to a computationally bounded prover and/or verifier. To realise a succinct argument system, the chosen commitment scheme must provide low communication complexity relative to the computation being proven.

Figure 1: A
正式定义
定义 1.1(承诺方案)。 承诺方案是 PPT 算法的元组
采用安全参数 (一元)并生成公共参数 ; 获取秘密消息 并输出公开承诺 和(可选)秘密打开提示 (可能为随机数)。 利用打开提示 ,验证承诺 对消息 的打开。
承诺方案
通俗来说,这意味着如果没有对手可以生成某个不同的消息
承诺方案
通俗来说,如果在承诺方案中,没有人能够“逆向工程”以确定到底是哪一条消息被承诺了,那么该承诺具有隐藏性。
回忆一下:“上锁的盒子”。 [第3讲:“数学基础构件”]
在汉密尔顿回路示例中,我们使用抗碰撞的哈希函数来构建我们的承诺方案:
是输入到哈希函数的随机采样密钥。 Commit:
。 Open: 检查
.
英文原文
Definition 1.1 (Commitment scheme). A commitment scheme is a tuple
takes security parameter (in unary) and generates public parameters ; Commit
takes a secret message and outputs a public commitment and (optionally) a secret opening hint (which might or might not be the randomness used in the computation). Open
verifies the opening of the commitment to the message provided with the opening hint .
A commitment scheme
Informally, this states that a valid commitment
A commitment scheme
Informally, this states that if a commitment is hiding if an adversary cannot "reverse-engineer" which of their messages was committed to.
Recall: "locked boxes". [Lecture 3: "Mathematical Building Blocks"]
In the Hamilton cycle example, we use a collision-resistant hash function to construct our commitment scheme:
is a randomly sampled secret key that is input to the hash function. Commit: hash
. Open : check
.
构造 Constructions
向量承诺 Vector commitment scheme
针对消息集
定义 2.1(位置绑定)。对于任何 PPT 敌手
通俗来说,没有任何敌手可以在同一个位置上用两个不同的值打开
向量 Pedersen 承诺。Pedersen 承诺[9]是一个在消息空间
Pedersen.Setup
,其中 是一个阶为 的群。 Pedersen.Commit
,其中 是一个秘密随机值。 Pedersen.Open
证明者 揭示 和 ,验证者 检查 。
需要注意的是,Pedersen 承诺具有加法同态性:
练习
证明 Pedersen 承诺方案是具有隐藏性和绑定性的。
请注意,在群
隐藏性:在给定承诺
的情况下,每个值 是否均等地有可能成为 对应的隐藏值? 绑定性:证明者是否能够找到
,使得 Pedersen.Commit Pedersen.Commit ?
我们可以将 Pedersen 承诺方案扩展到消息空间
VectorPedersen.Setup
,其中 是一个阶为 的群。 VectorPedersen.Commit
,其中 是一个秘密随机值。 VectorPedersen.Open
证明者 揭示 和 ,验证者 检查 。
练习
证明 VectorPedersen 是具有加法同态性,即
Merkle 树。一个常用的构建向量承诺的解决方案是 Merkle 树 [8]。它被用于像 Git、Cassandra 和 Bitcoin 这样的分布式系统中用于汇总数据集。Merkle 树也具有隐藏性和可提取性,这些安全特性使它成为在随机预言机模型中将 IOP 编译为非交互式证明的理想选择 [1]。
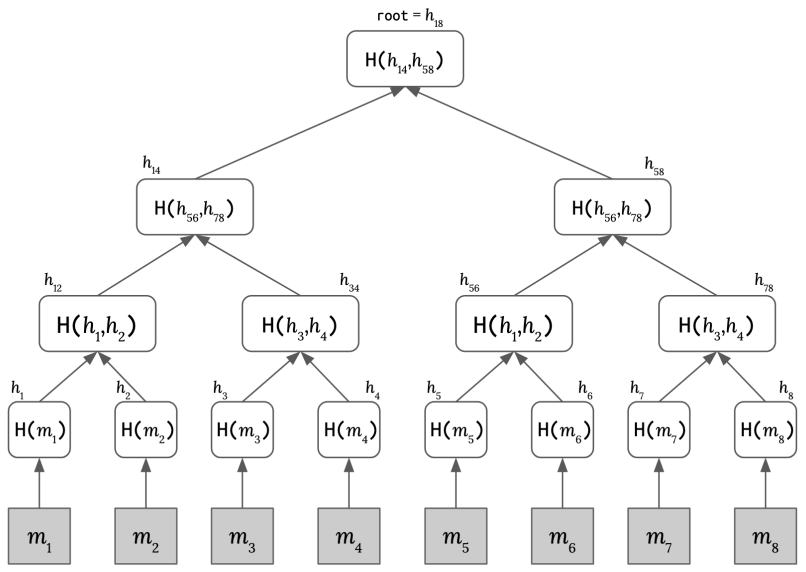
图 2:Merkle 树的每个内部节点都是其两个子节点的哈希值。
Merkle.Commit
:对于 中的每个 ,计算哈希值 。计算 Merkle 树的内部节点 。输出 。 Merkle.Open
: a) 证明者
计算从 到根节点的内部节点路径,并得到证据 。 b) 验证者
检查根节点是否可以通过将 和路径一起计算哈希得到。
英文原文
A vector commitment scheme [2] for the message space
Definition 2.1 (Position binding). A vector commitment scheme
Informally, this states that no adversary can open
Vector Pedersen commitment. The Pedersen commitment [9] is a binding and hiding commitment scheme for the message space
Pedersen.Setup
, where is a cryptographic group of order . Pedersen.Commit
, where is a random secret. Pedersen.Open
the prover reveals and , and the verifier checks
Note that the Pedersen commitment is additively homomorphic:
Exercise. Convince yourself that the Pedersen commitment scheme is hiding and binding.
Note that a cryptographic group
hiding: given a commitment
, is every value equally likely to be the value committed in binding: can a prover find
such that Pedersen.Commit Pedersen.Commit ?
We can extend the Pedersen commitment scheme to get VectorPedersen over vectors in the message space
VectorPedersen.Setup
, where is a cryptographic group of . VectorPedersen.Commit
, where is a random secret. VectorPedersen.Open
the prover reveals and , and the verifier checks
Exercise. Convince yourself that VectorPedersen is additively homomorphic, i.e.
Merkle tree. A well-known solution for building vector commitments is a Merkle tree [8]. It is used in distributed systems like Git, Cassandra, and Bitcoin for summarizing sets of data. Merkle trees also have hiding and extractability properties, which make them an ideal candidate for compiling an IOP into a non-interactive proof secure in the random oracle model [1].

Figure 2: Each inner node of a Merkle tree is the hashed value of its two children.
Merkle.Commit
: for each , compute a hash . Compute the inner nodes of the Merkle tree . Output . Merkle. Open
:
a) the prover
b) the verifier
多项式承诺方案
单变量多项式承诺方案是针对消息空间
它支持证明已承诺多项式在特定点上的正确评估的知识论证。在多项式中可以编码许多信息:我们将在第 7 讲 (“算术化”)和第 8 讲(“PlonK 和多项式恒等式”)中看到,任意关系都可以表示为一个多项式。
KZG 承诺方案[6]。这在像 Sonic [7]、Marlin [3] 和 PlonK [4] 这样的协议中使用。(Marlin 和 PlonK 通过构建不同的多项式 IOP 对 Sonic 进行了改进)。
回忆:双线性映射密码学
给定循环群
双线性:
非退化: 对于生成元
和 , 是一个生成元。
在本讲中,我们将使用简写符号
KZG.Setup
: 设置 . 是一个秘密元素,必须在 Setup 后丢弃。 KZG.Commit
对于 . KZG.Open( srs,
: 为了在评估点 上打开对于声称值 的承诺 a) 证明者
计算商多项式 并向验证者发送 Commit ck; b) 验证者
检查 .
KZG.Open 中的 a) 和 b) 步骤经常被写成两个分开的算法:
- Open
: 返回关系的开放证明
- Verify
: 验证开放证明的正确性。
英文原文
A univariate polynomial commitment scheme is a commitment scheme for the message space
It supports an argument of knowledge for proving the correct evaluation of a committed polynomial at a given point. A lot of information can be encoded in a polynomial: we will see in Lecture 7 ("Arithmetizations") and Lecture 8 ("PlonK and polynomial identities") how an arbitrary relation can be represented as a polynomial.
KZG commitment scheme [6]. This is used in protocols like Sonic [7], Marlin [3], and PlonK [4]. (Marlin and PlonK improve on Sonic by constructing a different polynomial IOP.)
Recall: Pairing-based cryptography. [Lecture 3: "Mathematical Building Blocks"]
Given cyclic groups
a) bilinear:
b) nondegenerate: with generators
In this lecture, we will use the shorthand notation
KZG.Setup
srs: set srs here is a secret element and must be discarded after the Setup. KZG.Commit
for . KZG.Open(srs,
: To "open" the commitment at evaluation point to a claimed value
a) the prover
b) the verifier
The a) and b) steps in KZG.Open are often written as two separate algorithms:
- Open
returns an opening proof for the relation
- Verify
verifies the opening proof's correctness.
额外资源
本笔记旨在作为承诺方案的高级介绍,并介绍它们在现代 SNARK 建设中的应用。以下是一些进一步了解和比较承诺方案的优秀资源:
英文原文
This note hopes to serve as a high-level introduction to commitment schemes, and where they fit in the construction of modern SNARKs. Below are a few excellent resources for further understanding and comparing commitment schemes:
更多的多项式承诺方案
多项式承诺:通用 SNARK 的构建块 (Justin Drake):基于使用的加密原语(哈希函数、配对群、未知阶群和离散对数群)对多项式承诺方案进行分类的结构分类。 (部分
和 。 KZG 多项式承诺 (Dankrad Feist):介绍了 KZG 多项式承诺方案,以及如何将其扩展到多证明和向量承诺。
内积证明 (Dankrad Feist):介绍内积证明 (IPA) 协议,一种可用于构建多项式承诺方案的原语。该 IPA 经常与向量 Pedersen 承诺方案一起实例化。
bulletproofs: :notes : inner_product_proof 有关 IPA 的出色介绍。
一个 STARK 的解剖,Part 3:FRI (Alan Szepieniec): 介绍 FRI (Fast Reed-Solomon IOP of Proximity) 协议,用于近距离的预言机证明。STARK 多项式 IOP 使用 Merkle 树实例化 FRI。
线性承诺工作在线性函数上。 (请注意,多项式承诺是线性承诺的一种特殊形式,因为
可以写为两个向量 和 的点积。)这些用于 Vortex(基于格的)、Brakedown 和 Orion 等构造。 多线性承诺对多变量线性多项式进行操作。它们可用于实例化 SumCheck 协议,这是一个既不是零知识也不是对 NP 声明有效的交互证明 (IP)。使用多线性承诺方案的 zk-SNARKs 包括:Hyrax、Libra、Virgo 和 Spartan。
英文原文
polynomial commitments: building block for universal SNARKS (Justin Drake): includes a taxonomy of polynomial commitment schemes based on the cryptographic primitives used (hash functions, pairing group, unknown order group, and discrete log group). (Parts
, and . KZG polynomial commitments (Dankrad Feist): an introduction to the KZG polynomial commitment scheme, and how to extend it to multiproofs and vector commitments.
Inner Product Arguments (Dankrad Feist): an introduction to the inner product argument (IPA) protocol, a primitive that can be used to build a polynomial commitment scheme. The IPA is often instantiated with the vector Pedersen commitment scheme.
bulletproofs: :notes : inner_product_proof excellent write-up on IPA.
Anatomy of a STARK, Part 3: FRI (Alan Szepieniec): an introduction to the FRI (Fast Reed-Solomon IOP of Proximity) protocol, an oracle proof of proximity. The STARK polynomial IOP instantiates FRI with Merkle trees.
Linear commitments work over linear functions. (Note that a polynomial commitment is a special form of a linear commitment, since
can be written as the dot product of two vectors and .) These are used in constructions like Vortex (lattice-based), Brakedown, and Orion. Multilinear commitments work over multivariate linear polynomials. They can be used to instantiate the sumcheck protocol, an interactive proof (IP) which is by itself neither zeroknowledge nor succinct for NP statements. zk-SNARKs which use the sumcheck protocol with multilinear commitment schemes include: Hyrax, Libra, Virgo, and Spartan.
实现和基准测试
arkworks-rs/poly-commit:一个 Rust 库,支持四种多项式承诺方案。
多项式承诺基准测试 (Remco Bloemen):基于 KZG、基于 IPA 和基于 FRI 的多项式承诺方案实现的 Commit 算法的基准测试。
英文原文
arkworks-rs/poly-commit: a Rust library supporting four polynomial commitment schemes.
Polynomial Commitment Benchmark (Remco Bloemen): benchmarks for the Commit algorithm in implementations of KZG, IPA-based, and FRI-based polynomial commitment schemes.